
by Chetan Sroay | Feb 1, 2025 | Cyber Security
Azure Security is a comprehensive framework designed to protect data, applications, and infrastructure hosted on Microsoft Azure. As organizations increasingly migrate to the cloud, understanding the security measures available within Azure becomes paramount. Azure...
by Chetan Sroay | Feb 1, 2025 | Cyber Security
Privileged Identity Management (PIM) is a critical aspect of cybersecurity that focuses on managing and securing accounts with elevated access rights within an organization. These privileged accounts, which can include system administrators, database administrators,...
by Chetan Sroay | Feb 1, 2025 | Cyber Security
In today’s digital landscape, understanding the risks associated with network security is paramount for individuals and organizations alike. Cyber threats come in various forms, including malware, phishing attacks, and ransomware, each designed to exploit...
by Chetan Sroay | Jun 10, 2024 | Cyber Security
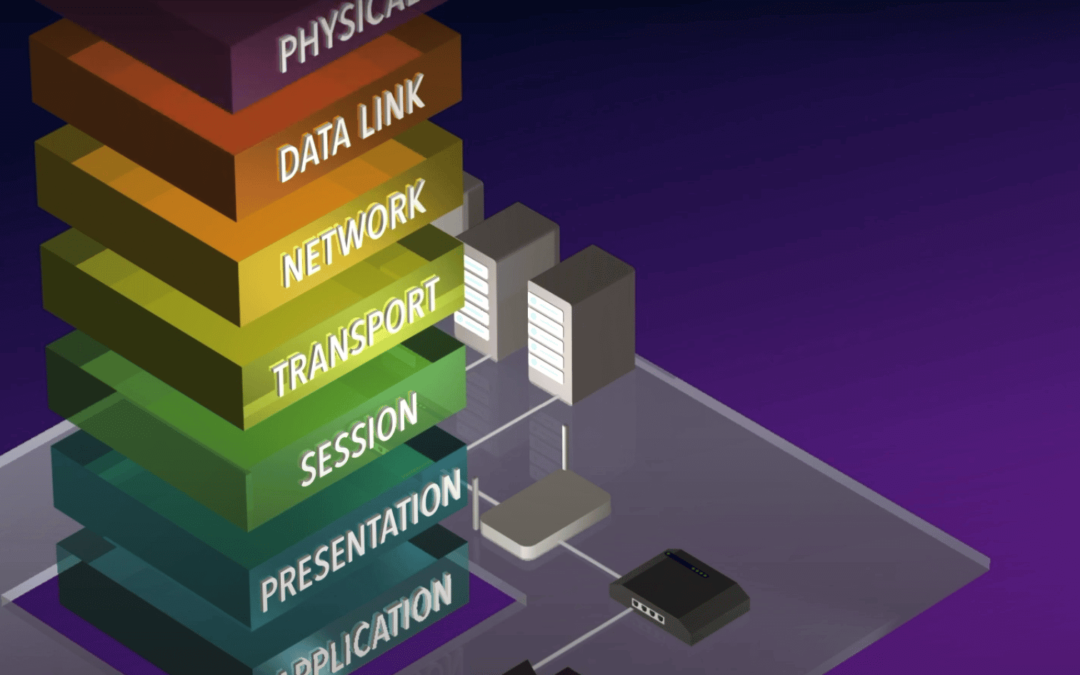
In the world of networking and cloud security, the OSI (Open Systems Interconnection) model is a fundamental concept that every IT professional should understand. This model provides a framework for understanding how different networking protocols interact and work...





